Ce site utilise des "cookies" afin d'optimiser la visite de notre site. En continuant de naviguer sur ce site, vous acceptez ceci.
Achieving security end to end
Defence in depth for the world's most demanding applications
Across the globe we are seeing strategic infrastructure owners investing heavily to improve networked resiliency and achieve greater climate neutrality. The need for the more resource-efficient control and optimization of processes has never been more pressing as we respond to the large-scale deployment of electric cars and integrations with a range of decentralised renewable technologies. Increasing levels of integration and therefore digitalization will result in unprecedented levels of interactions with digital assets from a large and diverse set of stakeholders. With many more distributed edge devices, the need for deeper security across devices, the network, the cloud, and connected systems has never been more critical and of more strategic importance.

Securing infrastructure in an insecure world
The surge in cyberattacks on infrastructure like power and water companies intensifies the need to take a new approach to security. The attacker who tried to poison a Florida city's water supply in 2021 was stopped by a vigilant supervisor, but later analysis of the water company';s infrastructure found even more vulnerabilities that had gone undetected.
Attacks on state-owned utilities in Brazil resulted in the theft of more than a thousand gigabytes of sensitive internal data, which attackers offered for sale. The same criminals went on to disable the Colonial Pipeline, which supplies almost half of the fuel needs of America’s East Coast. While most of the $4.4 million ransom paid was recovered by the FBI, it was too late to stop the panic-driven petrol shortages as motorists raced to fuel up.
Pressures within and without
Infrastructure companies face pressure from more than just attackers. They must also:
• abide by legislation, such as Europe’s Network & Information Systems (NIS) Directive, which tightens requirements to secure their systems and limit damages from any attacks; fines for non-compliance can exceed €19 million
• advance digital transformation initiatives that will support the smart grid and smart city, and improve the customer experience
• drive efficiencies with improved remote access for authorised engineers, without leaving doors open for attackers.
• leverage their investment in extensive legacy equipment that’s still fit for purpose
Critical Infrastructure companies must be better connected than ever to deliver on their strategic objectives. What’s needed is a new approach to securing that connectivity, to deliver protection at all levels.
Defending against attack with Defence in Depth
The concept of Defence in Depth is borrowed from the military. In the context of securing the infrastructure provider’s communications network, this means:
• deploying an enriched cybersecurity architecture with multiple redundant solutions
• using several independent methods to achieve layers of protection
• recognising and prioritising the network’s weakest point: remote assets
With Defence in Depth as its default design strategy for IT and Operational Technology systems - from RTU to SCADA master and everything in between - the provider can:
• leverage automation to secure its infrastructure at scale and at pace
• trust that individual devices can self-protect and self-isolate in the event of attack
• integrate with industry standards and recognised cybersecurity protocols and tools
Security from the bottom up: protect the weakest points
Attackers often avoid highly-defended Network Operations Centres and instead try to hijack remote assets. They may attempt to spoof their identity and modify routers that connect RTUs and other remote systems to the wide area network, and onwards to the NOC.
Each connected device must be capable of defending itself. This makes the WAN gateway a vital first line of defence.
Self-defence for connected remote assets
Infrastructure providers are increasingly deploying hardened WAN gateways that do more than just provide modem capability and protocol conversion for the RTUs, switches, and other mechanical infrastructure across their estates. To stay ahead of cybersecurity threats and risk of financial loss, they’re seeking solutions that offer microcontroller-level security, isolated cryptographic engines, and advanced capability to monitor, deploy and defend every connected device.
The Merlin series from Westermo- security from the bottom up
Developed by Westermo, the Merlin series of industrial cellular routers for remote sites are the first in the industry to feature comprehensive hardware-level cybersecurity, including:
Tamper-proof secure boot: highly secure boot process that prevents the router from functioning unless it can validate the digital signature of the router’s operating system.
Trusted Platform Module: this microcontroller-based chip keeps cryptographic keys separate from the file system. If the device is stolen, the keys cannot be retrieved. TPM also securely identifies the device to the network and supports standard cryptographic engines.
Zero-touch deployment: the router’s management software is Activator, which pioneered the zero-touch deployment methodology. Manage and update thousands of devices securely from one management domain, and automate asset verification for security at scale.
Network and inventory monitoring: the router’s alerting system presents the full operational state of the device and provides early warning of anomalies that could indicate an attack, such as spikes in a device’s CPU activity or network traffic loads.

Securing end-to-end communications
Infrastructure that supports end-to-end encryption gives providers another layer to a Defence in Depth design strategy. The Merlin series simplifies encryption at scale, even in complex legacy environments, and supports the latest encryption algorithms:
• Transport Layer Security (TLS – IEC32351-3 extension): encrypts traffic from the gateway at the remote site to the SCADA master at the Network Operations Centre
• IP Security Virtual Private Network (IPsec VPN): provides additional security across the wide-area network for sensitive traffic
• Supports flex VPN, Open VPN, and auto-enrolment with PKI (SCEP)
• Private keys used for VPN are protected with Trusted Platform Module
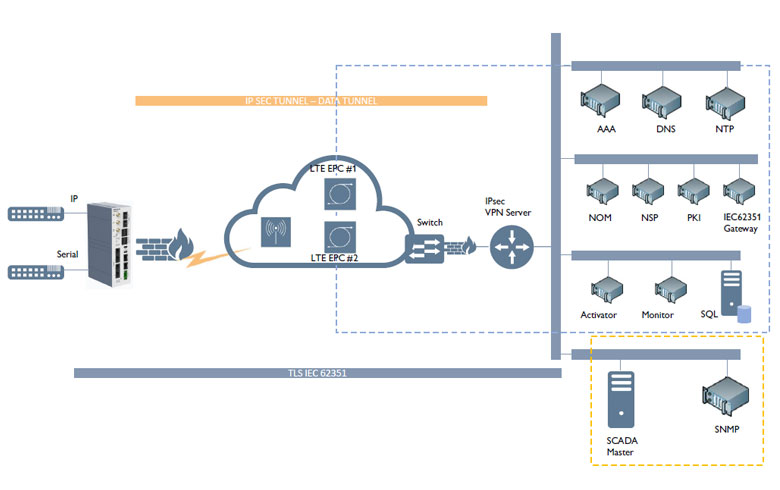
As providers prepare for initiatives like the smart grid that demand more visibility and control, there’s growing interest in private LTE networks as an alternative to commercial mobile networks. In a private LTE scenario, the utility operator’s wireless traffic runs over a dedicated network built on spectrum allotted by the communications regulator. Private LTE also keeps sensitive information on the internal WAN, instead of using commercial infrastructure that cyber-attackers may be more likely to target.
Typically, the 450Mhz or 410Mhz spectrums are made available for private LTE. One characteristic of this spectrum is the benefit of better penetration and reach compared to the higher frequencies found in commercial LTE networks. Using LTE bands that are not normally accessible to the public ensures that sensitive information is kept separate from the public domain and provides an additional level of defence that will defeat all but the most determined cyber attackers.
Westermo and private LTE
The Activator zero-touch platform has been used to deploy large-scale utility networks for customers operating private LTE networks, in many instances scaling in excess of 10,000 sites.
Westermo customers are implementing private LTE for connectivity and control of applications including:
• Smart grid
• Distribution automation
• Smart metering aggregation
• SCADA
The Merlin series includes features designed to meet the proven needs of utilities:
• TPM for security
• Integrated RTU/SCADA protocols that reduce need for external RTUs and simplify large deployments
• High galvanic isolation for longer life in electrically hostile environments
• Support for TLS and IPsec encryption – TLS has been shown in a research study funded by the University of Strathclyde Power Networks Demonstration Centre to consume less bandwidth; useful where bandwidth conservation is a priority.
More applications to explore

Implementing IEC 62351
IEC 62351 is an industrial standard for improving security in industrial systems, specifically in power systems.

Secure boot in OT networks
Secure boot is the ideal solution for protecting software components from attacks and ensuring the authenticity of running systems.

Achieving security end to end
With many more distributed edge devices, securing the devices, network, cloud, and connected systems has never been more critical.
Explorez toutes les solutions d'accès à distance
Depuis des décennies, nous proposons des produits et des solutions pour les applications de réseaux d'accès à distance. Grâce à notre vaste gamme de produits et à notre connaissance approfondie des applications, nous sommes en mesure de proposer la meilleure solution pour vos besoins.

Accès à distance pour les applications utilitaires
La connectivité cellulaire permet de surveiller les sites de manière globale.

Accès distant pour les applications industrielles
Obtenez une vue d'ensemble des sites qui étaient autrefois habités ou relativement invisibles.

Cyber-sécurisation des réseaux distants
Il n'a jamais été aussi important de garantir la sécurité de vos réseaux et systèmes industriels distants.

Réseaux Zero Touch
Déployer et assurer la maintenance de milliers de routeurs de manière rentable.

Conversion de protocole
La conversion de protocole permet de transmettre ou de recevoir un flux commun de données vers le SCADA Supérieur.

Remplacement du modem existant
Faites migrer les anciens dispositifs série des communications par modem commuté ou ligne louée vers la série sur IP à large bande.
Carl de Bruin
International sales

Pour toute requête technique, merci de vous orienter vers le contact support
